Turn applies FCRA, EEOC, SOC2, and PBSA standards to every check; no guesswork, no gaps, just peace of mind.
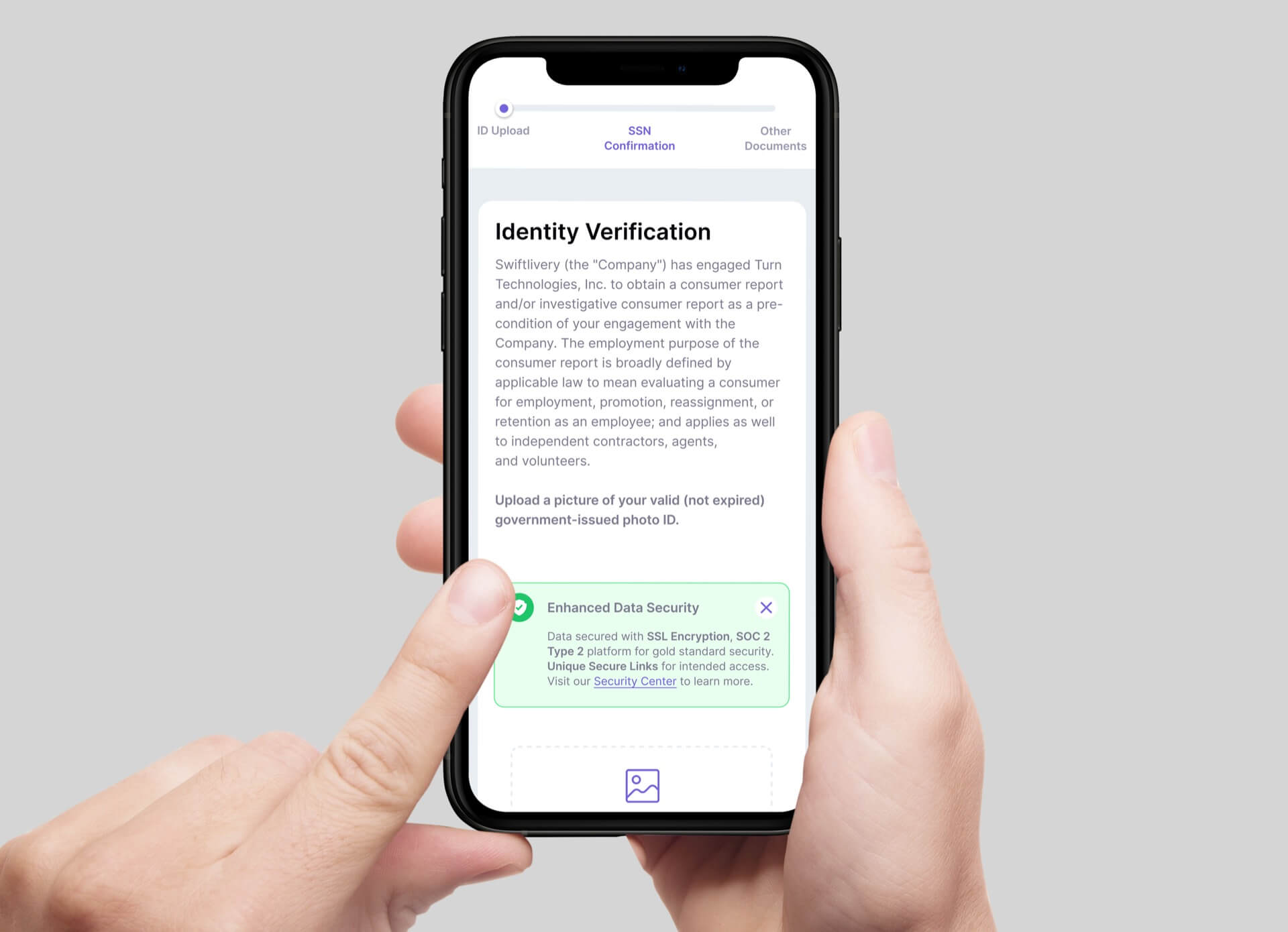
















Turn uses enterprise-grade practices to protect customer data, verified by independent experts and backed by a SOC 2 security and compliance report.
We use advanced encryption to protect all data we access, send, or store, so even in a breach, sensitive information remains unreadable and secure.
We never sell or share consumer, partner, or candidate data. Internally, access is tightly controlled and protected by our dedicated security teams.

Tailor-made for the high-volume hiring of hourly, salaried, shift-based, or independently contracted workers.

In various industries, drug testing plays a pivotal role in upholding a secure work atmosphere.

Operating seamlessly in the background, actively informs you of any significant updates to your workers’ records.

Turn will continuously monitor your workforce for speeding tickets, license suspensions, and DUIs.
High-margin pricing structure. Create a profitable stream with optimized partner pricing.
Most checks complete in under 1 hour, 80% within 24 hours; industry-best performance.
AI and human expertise, perfectly aligned for speed, accuracy, and trust.
Built for high-volume hiring of hourly, salaried, shift, and contract workers.
Phone, chat, and email support for both employers and candidates, in English and Spanish, fast and effective.
Deliver a seamless candidate experience with frictionless ATS/HRIS integrations or Turn’s powerful API, built for speed and simplicity.


























Monetize screening instantly with a plug-and-play solution. Turn runs the engine, you own the experience. We handle everything, compliance, processing, customer support, and dispute resolution. Just connect and profit.
Altar’d State streamlined hiring with Turn, improving efficiency and hire quality while cutting screening costs by 40%.
Culinary Agents improved UX, cut hiring friction, and deepened trust by embedding background checks into their platform.
Collective Retreats cut costs and sped up hiring with Turn, with a 1d 18h turnaround and 94% candidate conversion rate.
Syberg’s sped up hiring and reduced risk with Turn’s fast and affordable screening, boosting efficiency across locations.
Turn makes background checks fast, easy, and affordable. Request a free demo to see how.

Free Consultation, No Strings.
Fill in your info and we’ll reach out shortly.
Want a Closer Look for Free?
Connect with a Turn expert to experience the unmatched speed, exceptional affordability, and next-generation technology that set our platform apart.
Connect with a Turn expert to see faster, more affordable screening.
Let’s tailor a solution for you.
Tell us what you need and we’ll make ir work.
Let’s tailor a solution for you.
Tell us what you need and we’ll make ir work.
Learn how to hire faster and pay less.
Learn how to hire faster and pay less.
Learn how to hire faster and pay less.
Learn how to hire faster and pay less.